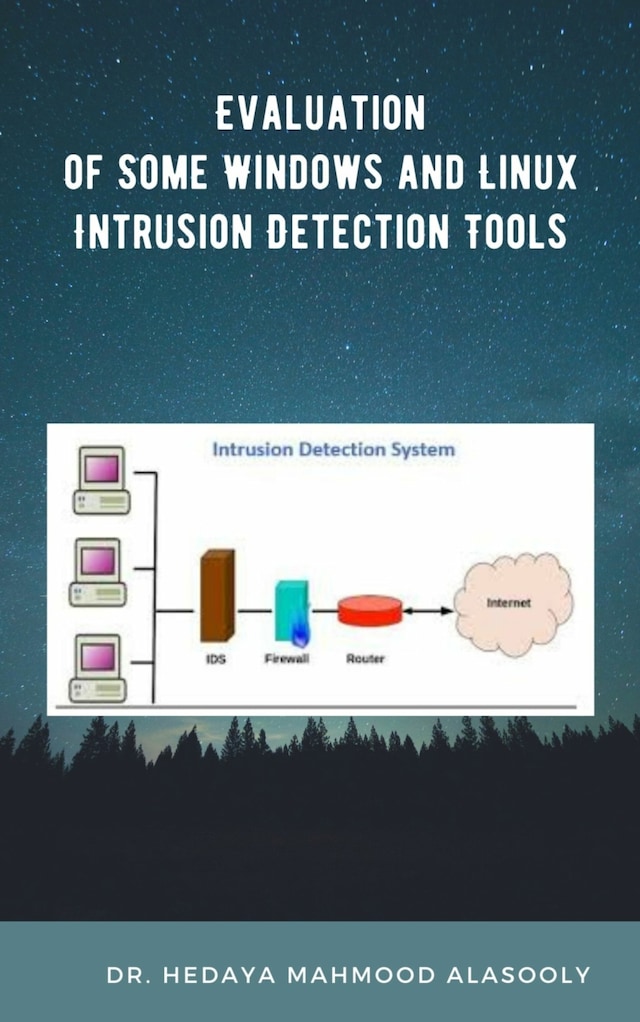
Evaluation of Some Windows and Linux Intrusion Detection Tools

